

Did you know that 76% of organizations have fallen victim to cyberattacks initiated through unknown or poorly managed external assets? What's more, a staggering 30% of assets lurking within customer environments remain unknown to security teams.
With the average cost of a data breach soaring to nearly $5 million dollars last year, the question arises: How can you safeguard what you cannot see?
Enter Attack Surface Intelligence. By enhancing asset visibility, prioritizing vulnerabilities for remediation, and fortifying security controls, organizations can confidently mitigate risks and defend against cyber threats. Additionally, automated and human-operated continuous penetration testing ensures ongoing compliance with industry standards and regulations. Protect your digital assets and safeguard your business with Attack Surface Intelligence today.
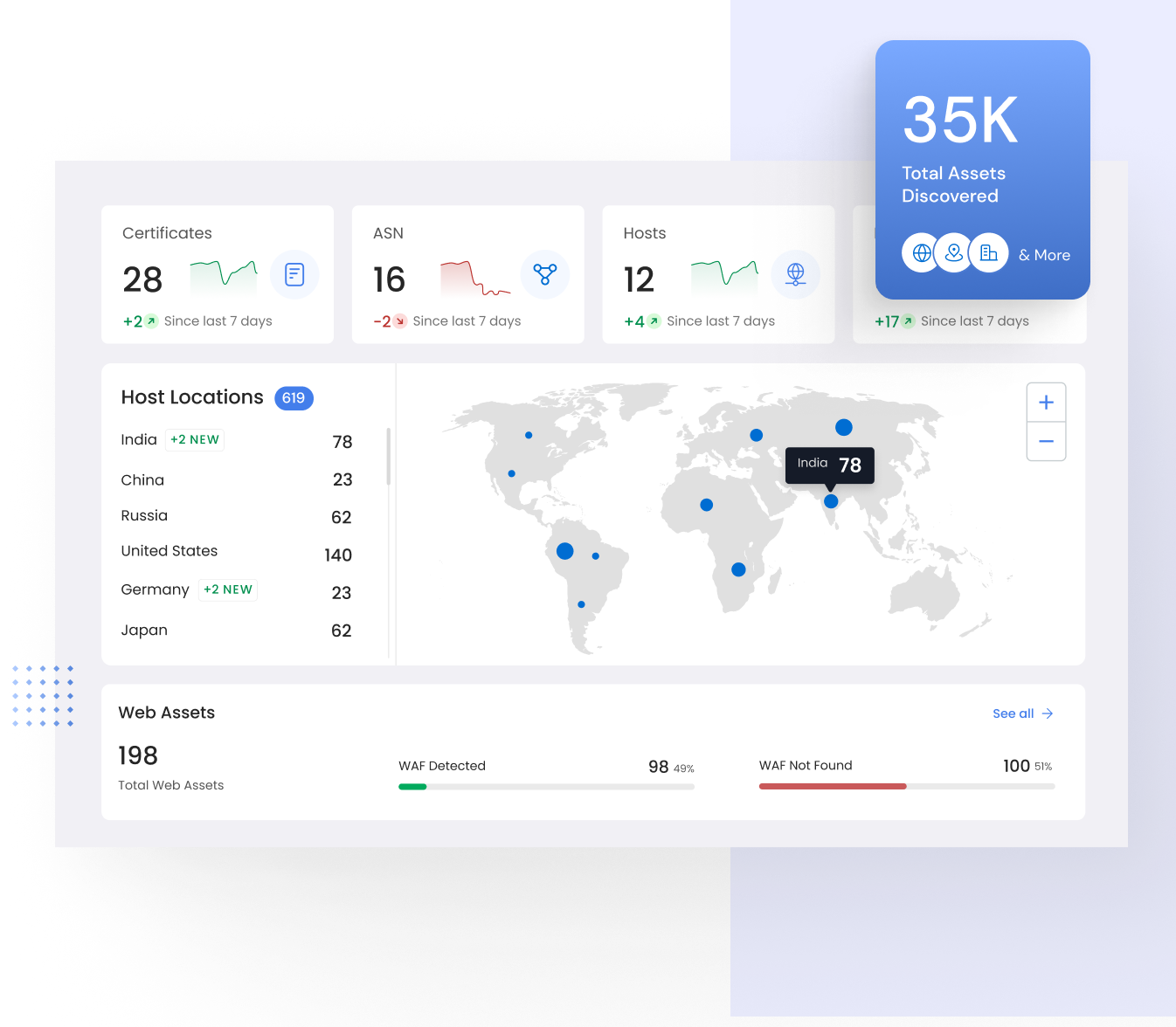

Gain a comprehensive understanding of your digital assets and their impact from the outset. With your organization mapped from day one, visualize your digital footprint from a bird's-eye view down to individual asset specifics.
Visualize your attack surface from an attacker's perspective, pinpointing your most vulnerable areas. Utilize exposure data sourced from vulnerabilities, operational technology, user behavior, compromised systems, public disclosures, and configurations across network, API, software, and the web.


With thousands of known vulnerabilities worldwide, it's crucial to ensure your protection. Gain a comprehensive understanding of your exposure across the extended enterprise as new vulnerabilities emerge.
Break the cycle of repeatedly addressing the same findings. Continuously evaluate the effectiveness of your security controls to fortify your defenses against cyber attacks and streamline operations.


Empower your security efforts with our comprehensive platform, offering both automated and human-operated penetration testing capabilities.
Affordable and easy to use security solution
Ricky Arora,
Co-founder, Observo.ai
Features
Assets (Web, API, Network)
Key Testing Features
Web Application Discovery & Testing (8000+ Test Cases (OWASP Top 10 & CWE Top 25, SANS, etc))
Internal Applications (Scanning Internal Applications)
External Applications (Scanning Publicly Available Applications)
JavaScript (Crawling through all integrated scripts)
Fingerprinting (Technology based Test Cases)
Crawler (Crawling all available endpoints)
Smart Recon (Dark Web, Open Source, Clear Web, Wayback, etc)
API Security Testing (SOAP, REST, GraphQL API)
Network Discovery & Testing ( 50,000+ Test Cases )
Business Logic Security Review
Proof of Exploit
Interactive Application Security Testing
Software Composition Analysis
Authenticated Scanning
Out-of-band vulnerability testing
Secure Code Review (SAST)
Cloud Security Review (AWS, Azure, GCP)
Compliance Review ( SOC2, ISO27001, PCI-DSS, HIPAA, GDPR)
Vulnerability Retest
Scan Management and Reporting
Number of Users
Executive dashboards
Full detailed scan report (including technical details about the vulnerabilities)
Remediation Advice
Flexible Support Options
Scheduled Scanning
Scans per Target
Publicly verifiable Pentest Certificate
Report Results
JSON
CSV
XML
Co-Branded Report (Add your company branding)
Whitelabelled Report (Reports with your branding)
Upto 10
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓ Upto 500 Functions
-
-
-
1
✓
✓
-
-
-
2
✓
✓
-
-
-
-
-
Upto 50
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓ Upto 1500 Functions
✓
✓
✓
3
✓
✓
✓
✓
✓
4
✓
✓
✓
✓
✓
✓
✓
Contact Sales
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
✓
Contact Sales
✓
✓
✓
Contact Sales
✓
✓
✓
✓
✓
Contact Sales
✓
✓
✓
✓
✓
✓
✓